Log Management
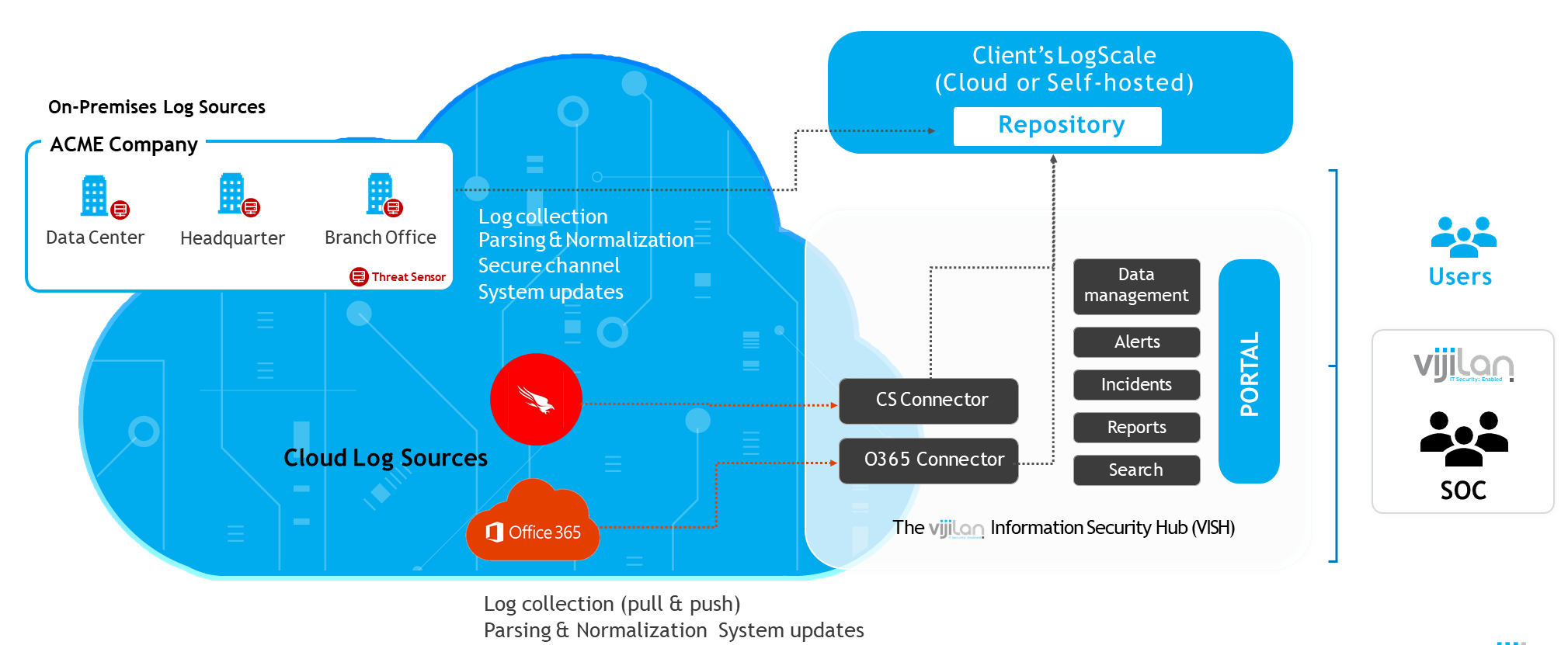
Our solution delivers continuous monitoring, supported by advanced technology and structured processes. Leveraging CrowdStrike Falcon LogScale for log management and Cribl for data ingestion and pipelining, we seamlessly collect and normalize logs from both on-premises and cloud sources. These logs are translated into standardized events, enriched with insights from Corelight Zeek and Suricata for deeper network visibility and threat detection, before being securely stored for their full lifecycle.
From data collection to rapid remediation, our platform integrates best-in-class tools to ensure comprehensive, real-time security that proactively protects your environment and simplifies log management across all assets.
Security data analytics
Elevate Your Security with Advanced Data Analytics
At Vijilan, our security data analytics platform goes beyond conventional monitoring to provide actionable insights and early detection of potential threats. By leveraging a combination of powerful data ingestion, log management, and advanced analytics, we enable organizations to proactively manage security across their entire digital ecosystem.
Key Features
- Real-Time Data Ingestion and Standardization
Using Cribl for streamlined data ingestion, we seamlessly collect logs from diverse sources, including on-premises systems, cloud environments, and hybrid networks. Each log is standardized and enriched for consistency, ensuring accurate analysis and clear insights.
- Comprehensive Log Management with CrowdStrike Falcon LogScale
Our platform utilizes CrowdStrike Falcon LogScale to manage and securely store logs, supporting compliance and providing a reliable, scalable solution for long-term log retention.
- Enhanced Threat Visibility
With Corelight Zeek and Suricata, we bring unparalleled visibility into network activities, empowering organizations to detect anomalies and threats before they escalate. Our analytics are built to identify complex attack patterns, enabling swift and effective threat response.
- AI-Powered Threat Intelligence
Leveraging the power of threat intelligence and AI-driven analysis, our platform continuously refines its detection capabilities, learning from every incident to stay ahead of emerging threats. This helps security teams focus on critical issues while avoiding alert fatigue.
- Seamless Integration with Existing Systems
Our analytics seamlessly integrate with Vijilan’s portal or your own ticketing and PSA systems, ensuring smooth workflows and enhanced productivity for security teams. This end-to-end integration streamlines alerting, triage, and response, optimizing incident handling.
Experience Complete, Proactive Security
Through advanced security data analytics, Vijilan empowers organizations to stay a step ahead of cyber threats, achieving proactive defense with precision and clarity. Our platform transforms raw data into strategic intelligence, keeping your environment secure and resilient.
Real-time detection
Real-Time Threat Detection
Stay Ahead with Vijilan’s Real-Time Threat Detection At Vijilan, our approach to real-time threat detection combines cutting-edge technology, continuous monitoring, and expert-driven processes to keep your organization secure. Our platform doesn’t just capture data; it transforms it into actionable insights that enable rapid, decisive responses to potential threats across all assets—endpoints, networks, identities, and cloud environments. How Our Real-Time Detection Works- Comprehensive Data Collection and Ingestion Using Cribl for data ingestion, Vijilan seamlessly gathers and standardizes logs from both on-premises and cloud sources. Each log is enriched and translated into a standardized format, enabling efficient analysis and creating a solid foundation for real-time threat detection.
- Leveraging CrowdStrike Falcon LogScale for Log Management Our partnership with CrowdStrike means we utilize Falcon LogScale for high-speed, scalable log management. This integration supports real-time event logging, giving us immediate insight into activity across all devices, workloads, and user interactions.
- Network and Endpoint Visibility Enhanced by Corelight Zeek and Suricata, Vijilan’s real-time detection delivers deep visibility into network behavior and endpoint activities. This combination detects anomalies, suspicious behaviors, and potential breaches early, providing full-spectrum coverage and minimizing security blind spots.
- Identity-Centric Detection and Analysis With identity being a central attack vector, Vijilan uses advanced identity analytics to track suspicious behavior, such as lateral movement and privilege misuse. Through our identity module, we provide insights into high-risk activity, protect against identity-driven attacks, and align with zero-trust principles to safeguard user and device access.
- Accelerated Threat Response and Remediation With ThreatRemediate, Vijilan goes beyond detection to offer full remediation capabilities. For lean teams, this means we handle containment and response on your behalf, stopping breaches in their tracks and maintaining continuity across your operations.